Aug 15, 2022
TechnologySteps
Install sddm:
# pacman -S sddm xorg
After reboot, examine the kernel and the sg1 pci infos:
[root@archvfio ~]# lspci | grep -i vga
00:01.0 VGA compatible controller: Red Hat, Inc. Virtio GPU (rev 01)
07:00.0 VGA compatible controller: Intel Corporation SG1 [Server GPU SG-18M] (rev 01)
[root@archvfio ~]# uname -a
Linux archvfio 5.19.1-arch2-1 #1 SMP PREEMPT_DYNAMIC Thu, 11 Aug 2022 16:06:13 +0000 x86_64 GNU/Linux
Add virtio gpu into blacklist:
# vim /etc/modprobe.d/blacklist.conf
# blacklist virtio_gpu
Didn’t take effects, change the graphical to qxl and added blacklist qxl:
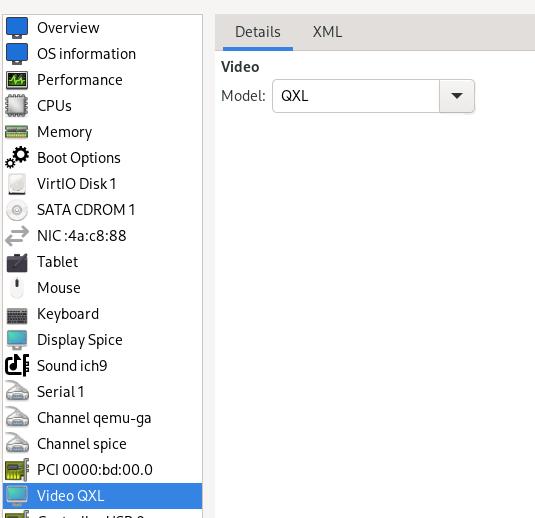
Take effects:
[root@archvfio ~]# lsmod | grep qxl
[root@archvfio ~]# ls /dev/dri/
by-path card0 renderD128
Examine the sg1 connected info:
for p in /sys/class/drm/*/status; do con=${p%/status}; echo -n "${con#*/card?-}: "; cat $p; done
DP-1: disconnected
DP-2: disconnected
DP-3: disconnected
HDMI-A-1: disconnected
HDMI-A-2: disconnected
HDMI-A-3: disconnected
HDMI-A-4: disconnected
Edit the Xorg configuration files and start the benchmark:
# cat /etc/X11/xorgintel.conf
Section "Device"
Identifier "Device[0]"
BusID "PCI:7:0:0"
VendorName "Intel"
BoardName "DG1"
Option "AllowEmptyInitialConfiguration"
EndSection
Section "ServerFlags"
Option "Debug" "dmabuf_capable"
EndSection
Section "Monitor"
Identifier "Monitor0"
VendorName "Monitor Vendor"
ModelName "Monitor Model"
Option "IgnoreEDID"
EndSection
# Xorg :179 -config /etc/X11/xorgintel.conf
# ps -ef | grep -i xorg
root 841 526 0 14:27 tty2 00:00:00 /usr/lib/Xorg :179 -config /etc/X11/xorgintel.conf
root 877 873 0 14:28 pts/1 00:00:00 grep -i xorg
testing
Install x11vnc and glmark2 for benchmarking:
# vim /etc/pacman.conf
[archlinuxcn]
#The Chinese Arch Linux communities packages.
SigLevel = Never
Server = http://repo.archlinuxcn.org/$arch
# pacman -Sy
# pacman -S x11vnc glmark2
[root@archvfio ~]# export DISPLAY=:179
[root@archvfio ~]# glmark2
=======================================================
glmark2 2021.12
=======================================================
OpenGL Information
GL_VENDOR: Intel
GL_RENDERER: Mesa Intel(R) Graphics (SG1)
GL_VERSION: 4.6 (Compatibility Profile) Mesa 22.1.6
=======================================================
glmark2 result:
=======================================================
glmark2 2021.12
=======================================================
OpenGL Information
GL_VENDOR: Intel
GL_RENDERER: Mesa Intel(R) Graphics (SG1)
GL_VERSION: 4.6 (Compatibility Profile) Mesa 22.1.6
=======================================================
[build] use-vbo=false: FPS: 2386 FrameTime: 0.419 ms
[build] use-vbo=true: FPS: 3112 FrameTime: 0.321 ms
[texture] texture-filter=nearest: FPS: 3262 FrameTime: 0.307 ms
[texture] texture-filter=linear: FPS: 3452 FrameTime: 0.290 ms
[texture] texture-filter=mipmap: FPS: 3493 FrameTime: 0.286 ms
[shading] shading=gouraud: FPS: 3056 FrameTime: 0.327 ms
[shading] shading=blinn-phong-inf: FPS: 3070 FrameTime: 0.326 ms
[shading] shading=phong: FPS: 2990 FrameTime: 0.334 ms
[shading] shading=cel: FPS: 3129 FrameTime: 0.320 ms
[bump] bump-render=high-poly: FPS: 2409 FrameTime: 0.415 ms
[bump] bump-render=normals: FPS: 3495 FrameTime: 0.286 ms
[bump] bump-render=height: FPS: 3393 FrameTime: 0.295 ms
[effect2d] kernel=0,1,0;1,-4,1;0,1,0;: FPS: 2885 FrameTime: 0.347 ms
[effect2d] kernel=1,1,1,1,1;1,1,1,1,1;1,1,1,1,1;: FPS: 2300 FrameTime: 0.435 ms
[pulsar] light=false:quads=5:texture=false: FPS: 3424 FrameTime: 0.292 ms
[desktop] blur-radius=5:effect=blur:passes=1:separable=true:windows=4: FPS: 1861 FrameTime: 0.537 ms
[desktop] effect=shadow:windows=4: FPS: 2431 FrameTime: 0.411 ms
[buffer] columns=200:interleave=false:update-dispersion=0.9:update-fraction=0.5:update-method=map: FPS: 769 FrameTime: 1.300 ms
[buffer] columns=200:interleave=false:update-dispersion=0.9:update-fraction=0.5:update-method=subdata: FPS: 1275 FrameTime: 0.784 ms
[buffer] columns=200:interleave=true:update-dispersion=0.9:update-fraction=0.5:update-method=map: FPS: 824 FrameTime: 1.214 ms
[ideas] speed=duration: FPS: 3128 FrameTime: 0.320 ms
[jellyfish] <default>: FPS: 2708 FrameTime: 0.369 ms
[terrain] <default>: FPS: 509 FrameTime: 1.965 ms
[shadow] <default>: FPS: 2664 FrameTime: 0.375 ms
[refract] <default>: FPS: 1041 FrameTime: 0.961 ms
[conditionals] fragment-steps=0:vertex-steps=0: FPS: 3226 FrameTime: 0.310 ms
[conditionals] fragment-steps=5:vertex-steps=0: FPS: 3035 FrameTime: 0.329 ms
[conditionals] fragment-steps=0:vertex-steps=5: FPS: 2974 FrameTime: 0.336 ms
[function] fragment-complexity=low:fragment-steps=5: FPS: 3014 FrameTime: 0.332 ms
[function] fragment-complexity=medium:fragment-steps=5: FPS: 3047 FrameTime: 0.328 ms
[loop] fragment-loop=false:fragment-steps=5:vertex-steps=5: FPS: 3250 FrameTime: 0.308 ms
[loop] fragment-steps=5:fragment-uniform=false:vertex-steps=5: FPS: 3050 FrameTime: 0.328 ms
[loop] fragment-steps=5:fragment-uniform=true:vertex-steps=5: FPS: 3293 FrameTime: 0.304 ms
=======================================================
glmark2 Score: 2665
=======================================================
Unigen valley benchmark:
# export DISPLAY=:179
[root@archvfio ~]# x11vnc
###############################################################
#@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@#
#@ @#
#@ ** WARNING ** WARNING ** WARNING ** WARNING ** @#
#@ @#
#@ YOU ARE RUNNING X11VNC WITHOUT A PASSWORD!! @#
#@ @#
#@ This means anyone with network access to this computer @#
On another terminal:
[root@archvfio ~]# export DISPLAY=:179
[root@archvfio ~]# cd Unigine_Valley-1.0/
[root@archvfio Unigine_Valley-1.0]# ls
bin data documentation valley
[root@archvfio Unigine_Valley-1.0]# ./valley
valley cannot start in default resolution, changes edid and set the default resolution to 1920x1080:
# vim /etc/default/grub
........
GRUB_CMDLINE_LINUX_DEFAULT="loglevel=3 quiet drm_kms_helper.edid_firmware=edid/1920x1080.bin video=HDMI-A-1:e"
........
# grub-mkconfig -o /boot/grub/grub.cfg
Valley result:
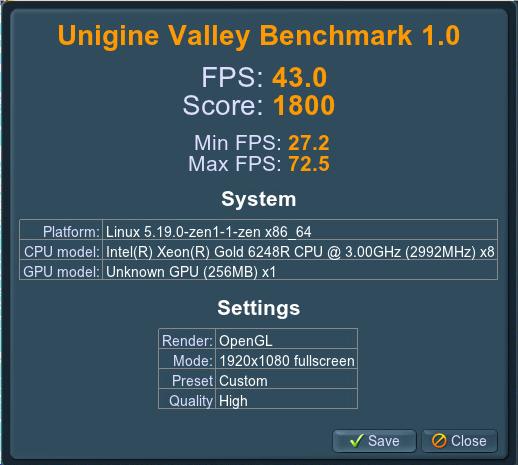
Benchmark results:
Time: 189.067
Frames: 8108
FPS: 42.8842
Min FPS: 25.3772
Max FPS: 71.5901
Score: 1794.28
Ubuntu sg1
Update and upgrade system(based on desktop iso):
# apt update && apt upgrade && apt install openssh-server vim glmark2 x11vnc && ufw disable && systemctl disable gdm && reboot
# vim /etc/modprobe.d/blacklist.conf
.......
blacklist qxl
Using linux-zen kernel:
Install the linux-zen via:
# sudo add-apt-repository ppa:damentz/liquorix && sudo apt-get update
# sudo apt-get install linux-image-liquorix-amd64 linux-headers-liquorix-amd64
root@dash-Standard-PC-Q35-ICH9-2009:/home/dash# ls /dev/dri/
by-path card0 renderD128
root@dash-Standard-PC-Q35-ICH9-2009:/home/dash# uname -a
Linux dash-Standard-PC-Q35-ICH9-2009 5.19.0-1.1-liquorix-amd64
Create Xorg via:
tobe added
Issue: not started:
error: Kernel is too old for Iris. Consider upgrading to kernel v4.16.
Ubuntu20.04 sg1
Install the kernel provided by intel, then:
# ln -s /usr/lib/x86_64-linux-gnu/dri/swrast_dri.so /usr/lib64/dri/swrast_dri.so
# ln -s /usr/lib/x86_64-linux-gnu/dri/kms_swrast_dri.so /usr/lib64/dri/kms_swrast_dri.so
# ln -s /usr/local/lib/x86_64-linux-gnu/dri/iris_dri.so /usr/lib64/dri/iris_dri.so
# export LD_LIBRARY_PATH=/usr/local/lib:/usr/local/lib64:/usr/local/lib64/dri:/usr/lib64/:/usr/lib64/dri:$LD_LIBRARY_PATH
# export MESA_LOADER_DRIVER_OVERRIDE=iris
# Xorg :179 -config /etc/X11/xorgintel.conf
X.Org X Server 1.20.13
X Protocol Version 11, Revision 0
Build Operating System: linux Ubuntu
Current Operating System: Linux virtio-vga-node 5.4.48-3c77c0f552c7+ #1 SMP Fri Jan 15 13:26:42 UTC 2021 x86_64
Kernel command line: BOOT_IMAGE=/boot/vmlinuz-5.4.48-3c77c0f552c7+ root=UUID=a10af00c-1048-4629-bfd7-e7aa7f2b4866 ro quiet splash vt.handoff=7
Build Date: 14 December 2021 02:14:13PM
xorg-server 2:1.20.13-1ubuntu1~20.04.2 (For technical support please see http://www.ubuntu.com/support)
Current version of pixman: 0.38.4
Before reporting problems, check http://wiki.x.org
to make sure that you have the latest version.
Markers: (--) probed, (**) from config file, (==) default setting,
(++) from command line, (!!) notice, (II) informational,
(WW) warning, (EE) error, (NI) not implemented, (??) unknown.
(==) Log file: "/var/log/Xorg.179.log", Time: Tue Aug 16 09:38:50 2022
(++) Using config file: "/etc/X11/xorgintel.conf"
(==) Using system config directory "/usr/share/X11/xorg.conf.d"
(II) modeset(0): Initializing kms color map for depth 24, 8 bpc.
MESA: warning: Driver does not support the 0x4907 PCI ID.
(II) modeset(0): Initializing kms color map for depth 24, 8 bpc.
MESA: warning: Driver does not support the 0x4907 PCI ID.
In another terminal , run glmark2:
# export DISPLAY=:179
# glmark2
UniValley result:
Time: 189.107
Frames: 7131
FPS: 37.7089
Min FPS: 19.6125
Max FPS: 68.0576
Score: 1577.74
Jul 26, 2022
TechnologySteps
Install necessray packages:
sudo apt install -y openjdk-8-jdk build-essential
sudo apt install git-core gnupg flex bison maven gperf build-essential zip curl zlib1g-dev gcc-multilib g++-multilib libc6-dev-i386 lib32ncurses5-dev x11proto-core-dev libx11-dev lib32z-dev ccache libgl1-mesa-dev libxml2-utils xsltproc unzip squashfs-tools libssl-dev ninja-build lunzip syslinux syslinux-utils gettext genisoimage gettext bc xorriso libncurses5 xmlstarlet build-essential git imagemagick lib32readline-dev lib32z1-dev liblz4-tool libncurses5-dev libsdl1.2-dev libxml2 lzop pngcrush rsync schedtool python3-mako libelf-dev$a
sudo apt-get install gcc-10 g++-10
git config --global user.email "you@example.com"
git config --global user.name "Your Name"
Get the repo from ustc.edu.cn, and replace the repo for proxy.
$ curl -sSL 'https://gerrit-googlesource.proxy.ustclug.org/git-repo/+/master/repo?format=TEXT' |base64 -d > ~/bin/repo
$ chmod a+x ~/bin/repo
## 如果提示无法连接到 gerrit.googlesource.com,可以编辑 ~/bin/repo,把 REPO_URL 一行替换成下面的:
## REPO_URL = 'https://gerrit-googlesource.proxy.ustclug.org/git-repo'
Repo init:
repo init -u https://github.com/BlissRoms-x86/manifest.git -b r11-r36
Repo sync(Using redsocks):
repo sync -j8
After repo sync:
cd prebuilts/gcc/linux-x86/host/x86_64-linux-glibc2.11-4.6
git checkout 2078a6bf9e5479104cfe2cbf54e9602672bd89f7
Build via:
. build/envsetup.sh
lunch android_x86_64-userdebug
export NO_KERNEL_CROSS_COMPILE=true
export BLISS_BUILD_VARIANT=foss
mka iso_img -j8
The generated iso is listed as:
out/target/product/x86_64/BlissOS-14.3-x86_64-202207270925_k-_m-r11-r36.iso is built successfully.
#### build completed successfully (02:40:00 (hh:mm:ss)) ####
dash@2204:/media/sda/Code/BlissOS$
dash@2204:/media/sda/Code/BlissOS$ ls out/target/product/x86_64/BlissOS-14.3-x86_64-202207270925_k-_m-r11-r36.iso
out/target/product/x86_64/BlissOS-14.3-x86_64-202207270925_k-_m-r11-r36.iso
Jul 25, 2022
TechnologyInstallation:
sudo qemu-system-x86_64 -name Arch -cdrom /var/lib/libvirt/images/ubuntu-20.04.3-live-server-amd64.iso -drive file=/var/lib/libvirt/images/vfioubuntu.qcow2 -m 8192 -enable-kvm -M q35 -cpu host -smp 4,sockets=1,cores=4,threads=1 -display egl-headless,gl=on -usb -device usb-tablet -bios /usr/share/OVMF/OVMF_CODE.fd -boot order=d -device virtio-vga,virgl=on -spice unix,disable-ticketing,image-compression=off,addr=arch.sock,seamless-migration=on
After installation, start the vm via:
sudo qemu-system-x86_64 -name Arch -drive file=/var/lib/libvirt/images/vfioubuntu.qcow2,if=virtio -m 22192 -enable-kvm -M q35 -cpu host -smp 8,sockets=1,cores=8,threads=1 -usb -device usb-tablet -device usb-ehci,id=ehci -bios /usr/share/OVMF/OVMF_CODE.fd -boot order=c -vga none -device virtio-gpu-pci,virgl=on -display sdl,gl=on -net nic -net user,hostfwd=tcp::2288-:22,hostfwd=tcp::5555-:5555
Jul 22, 2022
Technology1. 硬件信息
内存速度通过sudo dmidecode --type 17来检测
平台 1(i7 9代机器, 4核8线程,32G内存):
CPU: Intel(R) Core(TM) i7-9700K CPU @ 3.60GHz
Memory: MemTotal: 32709264 kB, 2666 MT/s
平台 2(i5 4代机器,4核4线程,32G内存):
CPU: Intel(R) Core(TM) i5-4460 CPU @ 3.20GHz
Memory: MemTotal: 32808212 kB, 1600 MT/s
测试中使用同一块sata ssd:
Disk 1: Crucial 500GB sata ssd.
测试显卡信息, 一块为WX5100 8G, 一块为5700 xt 8G(检测命令为 lspci | grep -i vga):
Card1: VGA compatible controller: Advanced Micro Devices, Inc. [AMD/ATI] Navi 10 [Radeon RX 5600 OEM/5600 XT / 5700/5700 XT] (rev c4)
Card2: VGA compatible controller: Advanced Micro Devices, Inc. [AMD/ATI] Ellesmere [Radeon Pro WX 5100]
2. 系统/软件信息
列举如下:
$ cat /etc/issue
Ubuntu 20.04.4 LTS \n \l
$ uname -a
Linux hope 5.4.0-120-generic #136-Ubuntu SMP Fri Jun 10 13:40:48 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
$ qemu-system-x86_64 --version
QEMU emulator version 6.0.0 (Debian 1:6.0+dfsg-2expubuntu1~focal1.0)
Copyright (c) 2003-2021 Fabrice Bellard and the QEMU Project developers
$ dpkg -l | grep -i virgl
ii libvirglrenderer-dev:amd64 0.8.2-1ubuntu1.1 amd64 virtual GPU for KVM virtualization - headers
ii libvirglrenderer1:amd64 0.8.2-1ubuntu1.1 amd64 virtual GPU for KVM virtualization
软件信息:
Unigine_Heaven-4.0
Unigine_Valley-1.0
glmark2
Redroid(Android 12)
scrcpy
3. 桌面场景测试
| 测试样例 | 目的描述 | 简要结论 |
|---|
| 3.1 裸机对比(WX5100) | 裸机opengl及游戏场景对比-WX5100 | 因WX5100算力一般,i5/i7表现差别不大 |
| 3.2 裸机对比(5700xt) | 裸机opengl及游戏场景对比-5700xt | i5平台成为测试中瓶颈位 |
| 3.3 Virgl On i5-4460(WX5100) | Virgl 性能对比 - i5-4460+WX5100 | glmark为主机的31.3%,因WX5100算力一般,游戏场景下Virgl未出现明显损耗 |
| 3.4 Virgl On i7-9700K(WX5100) | Virgl 性能对比 - i7-9700K+WX5100 | glmark为主机的44.2%,因WX5100算力一般,游戏场景下Virg未出现明显折损,平台算力能提升OpenGL算力 |
| 3.5 Virgl On i5-4460(5700xt) | Virgl 性能对比 - i5-4460+5700xt | glmark为主机的21%,1080P场景下为裸机的55%~60%, 4K场景下为裸机的87% |
| 3.6 Virgl On i7-9700K(5700xt) | Virgl 性能对比 - i7-9700K+5700xt | glmark为主机的19%,1080P场景下为裸机的55%~60%, 4K场景下为裸机的83% |
3.1 裸机对比(WX5100)
| i5-4460 | i7-9700K |
|---|
| glmark2 | 9140, 9117, 9117 | 9730, 9651, 9660 |
| Unigine_Valley FPS | 43, 42.4, 42.3 | 45.6, 45.0, 45.0 |
| Unigine_Valley Score | 1800, 1773, 1769 | 1906, 1884, 1884 |
| Unigine_Heaven FPS | 44.8 | 46.9 |
| Unigine_Heaven Score | 1130 | 1182 |
结论:
- i5/i7平台上,WX5100表现基本一致。
- 因WX5100算力比较一案,i5-4代没有成为测试中的瓶颈位。
3.2 裸机对比(5700xt)
| i5-4460 | i7-9700K |
|---|
| glmark2 | 13950, 14165, 14315 | 22134, 22256, 22150 |
| Unigine_Valley FPS | 105, 103.1, 102.9 | 168.7, 169.1, 168.5 |
| Unigine_Valley Score | 4391, 4315, 4304 | 7057, 7068, 7043 |
| Unigine_Heaven FPS | 167.0 | 171.1 |
| Unigine_Heaven Score | 4206 | 4311 |
| Unigine_Heaven FPS(4k) | 43 | 42.8 |
| Unigine_Heaven Score(4k) | 1083 | 1077 |
结论:
- 5700xt在i7平台上运行远比i5平台上流畅,4代i5平台无法发挥5700xt的算力特性,具体表现为:glmark2跑分差距较大,Unigine valley帧率相差较大(1080场景下掉了约70帧),4K下表现一致。
- 显卡选型时需充分考虑CPU/内存等平台算力特性。
3.3 Virgl On i5-4460(WX5100)
| i5-4460 | Virgl on i5-4460 |
|---|
| glmark2 | 9140, 9117, 9117 | 2892, 2859, 2827 |
| Unigine_Valley FPS | 43, 42.4, 42.3 | 40.8, 40.5, 40.6 |
| Unigine_Valley Score | 1800, 1773, 1769 | 1707, 1694, 1699 |
| Unigine_Heaven FPS | 44.8 | 42.2 |
| Unigine_Heaven Score | 1130 | 1062 |
结论:
- glmark2: Virgl跑分约为裸机的31.3%。
- Unigine场景跑分: Virgl性能并未出现明显折损,因为WX5100本身算力一般, CPU足够支撑virgl转码开销。
3.4 Virgl On i7-9700K(WX5100)
| i7-9700K | Virgl on i7-9700K |
|---|
| glmark2 | 9730, 9651, 9660 | 4274, 4262, 4320 |
| Unigine_Valley FPS | 45.6, 45.0, 45.0 | 42.3, 41.6, 41.5 |
| Unigine_Valley Score | 1906, 1884, 1884 | 1770, 1740, 1737 |
| Unigine_Heaven FPS | 46.9 | 41.9 |
| Unigine_Heaven Score | 1182 | 1055 |
结论:
- glmark2: Virgl 约为裸机跑分的44.2%。
- Unigine场景跑分: Virgl性能并未出现明显折损,因为WX5100本身算力一般, CPU足够支撑virgl转码开销。
- 提升平台算力(CPU,内存等)有助于提升opengl转码效率(对比3.3场景下glmark2跑分).
3.5 Virgl On i5-4460(5700xt)
| i5-4460 | Virgl on i5-4460 |
|---|
| glmark2 | 13950, 14165, 14315 | 2916, 3174, 2832 |
| Unigine_Valley FPS | 105, 103.1, 102.9 | 61, 61.9, 60.9 |
| Unigine_Valley Score | 4391, 4315, 4304 | 2551, 2588, 2548 |
| Unigine_Heaven FPS | 167.0 | 89.7 |
| Unigine_Heaven Score | 4206 | 2271 |
| Unigine_Heaven FPS(4k) | 43 | 37.8 |
| Unigine_Heaven Score(4k) | 1083 | 951 |
结论:
- glmark2: Virgl约为裸机的21%。
- Unigine Valley/Unigine Heaven: Virgl约为裸机跑分的55%~60%, 但在4K场景下,Virgl为裸机的87%。
3.6 Virgl On i7-9700K(5700xt)
| i7-9700K | Virgl on i7-9700K |
|---|
| glmark2 | 22134, 22256, 22150 | 4152, 4256, 4238 |
| Unigine_Valley FPS | 168.7, 169.1, 168.5 | 91.6, 91.5, 91.4 |
| Unigine_Valley Score | 7057, 7068, 7043 | 3831, 3829, 3825 |
| Unigine_Heaven FPS | 171.1 | 85.3 |
| Unigine_Heaven Score | 4311 | 2149 |
| Unigine_Heaven FPS(4k) | 42.8 | 35.6 |
| Unigine_Heaven Score(4k) | 1077 | 896 |
结论:
- glmark2: Virgl约为裸机的19%。
- Unigine Valley/Unigine Heaven: Virgl约为裸机跑分的55%~60%, 但在4K场景下,Virgl为裸机的83%。
4. Android 场景
| 硬件平台 | 跑分(开启scrcpy) | 跑分(不开启scrcpy) |
|---|
| i7-9700K+5700xt | 616521(剑侠山谷: 309760 , 禅院悟道: 306761) | 617133(剑侠山谷: 310050, 禅院悟道: 307083) |
| Virgl on (i7-9700K+5700xt) | 442043(剑侠山谷: 223850 , 禅院悟道: 218193) | 564343(剑侠山谷: 289202, 禅院悟道:275141) |
| i5-4460+5700xt | 384564(剑侠山谷: 112763 , 禅院悟道: 221801) | 592030(剑侠山谷: 283705, 禅院悟道: 308255) |
| Virgl on (i5-4460+5700xt) | 227747(剑侠山谷: 108206 , 禅院悟道: 119541) | 445234(剑侠山谷: 214831, 禅院悟道:230403) |
| i7-9700K+WX5100 | 567503(剑侠山谷: 265995 , 禅院悟道: 301508) | 585720(剑侠山谷: 277133, 禅院悟道: 308587) |
| Virgl on (i7-9700K+WX5100) | 412764(剑侠山谷: 210150 , 禅院悟道: 202614) | 499942(剑侠山谷: 257037, 禅院悟道: 242905) |
| i5-4460+WX5100 | 401626(剑侠山谷: 166695 , 禅院悟道: 234931) | 572952(剑侠山谷: 267744, 禅院悟道: 305208) |
| Virgl on (i5-4460+WX5100) | 225837(剑侠山谷: 106071 , 禅院悟道: 119766) | 445202(剑侠山谷: 211450, 禅院悟道:233752) |
结论:
- 鲁大师跑分极限: 约为60+万分,跑分时支持的最大分辨率为1080p(待确认)?
- scrcpy开启与否会影响跑分结果: 尤其在低端CPU上跑分下降尤为明显。
- 当GPU算力不至于成为瓶颈的场景下,virgl在安卓下渲染的跑分可以达到裸机极限跑分的: 90% (i7-9700K + 5700xt)
- WX5100可能成为跑分的性能瓶颈的场景下, virgl安卓渲染跑分在i7下可达到裸机极限的: 85% (i7-9700K + WX5100), i5下可达到裸机极限的: 77% (i5-4460 + WX5100)
Jul 22, 2022
Technology1. HardWare Info
Detect the memory speed via sudo dmidecode --type 17.
Hardware 1(i7 9th machine):
CPU: Intel(R) Core(TM) i7-9700K CPU @ 3.60GHz
Memory: MemTotal: 32709264 kB, 2666 MT/s
Hardware 2(i5 machine):
CPU: Intel(R) Core(TM) i5-4460 CPU @ 3.20GHz
Memory: MemTotal: 32808212 kB, 1600 MT/s
Use the same ssd disk:
Disk 1: Crucial 500GB sata ssd.
Disk 2: nvme ssd 256GB.
Graphical Card Info(Detected via lspci | grep -i vga):
Card1: VGA compatible controller: Advanced Micro Devices, Inc. [AMD/ATI] Navi 10 [Radeon RX 5600 OEM/5600 XT / 5700/5700 XT] (rev c4)
Card2: VGA compatible controller: Advanced Micro Devices, Inc. [AMD/ATI] Ellesmere [Radeon Pro WX 5100]
2. System/SoftWare Info
System and Software info listed as:
500GB Crucial ssd:
$ cat /etc/issue
Ubuntu 20.04.4 LTS \n \l
$ uname -a
Linux hope 5.4.0-120-generic #136-Ubuntu SMP Fri Jun 10 13:40:48 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
$ qemu-system-x86_64 --version
QEMU emulator version 6.0.0 (Debian 1:6.0+dfsg-2expubuntu1~focal1.0)
Copyright (c) 2003-2021 Fabrice Bellard and the QEMU Project developers
$ dpkg -l | grep -i virgl
ii libvirglrenderer-dev:amd64 0.8.2-1ubuntu1.1 amd64 virtual GPU for KVM virtualization - headers
ii libvirglrenderer1:amd64 0.8.2-1ubuntu1.1 amd64 virtual GPU for KVM virtualization
nvme ssd 256GB:
$ cat /etc/issue
Pop!_OS 21.10 \n \l
$ uname -a
Linux pop-os 5.17.15-76051715-generic #202206141358~1655919116~21.10~1db9e34 SMP PREEMPT Wed Jun 22 19 x86_64 x86_64 x86_64 GNU/Linux
$ qemu-system-x86_64 --version
QEMU emulator version 6.0.0 (Debian 1:6.0+dfsg-2expubuntu1.3)
Copyright (c) 2003-2021 Fabrice Bellard and the QEMU Project developers
$ dpkg -l | grep -i virgl
ii libvirglrenderer1:amd64 0.8.2-5ubuntu0.21.10.1 amd64 virtual GPU for KVM virtualization
Software:
Unigine_Heaven-4.0
Unigine_Valley-1.0
glmark2
Redroid(Android 12)
3. Desktop Scenario
| Case Lists | Description | Conclusion |
|---|
| 3.1 BareMetal Comparison(WX5100) | BareMetal Performance comparison using WX5100 | |
| 3.2 BareMetal Comparison(5700xt) | BareMetal Performance comparison using 5700xt | |
| 3.3 Virgl On i5-4460(WX5100) | Virgl Performance on i5-4460 using WX5100 | |
| 3.4 Virgl On i7-9700K(WX5100) | Virgl Performance on i7-9700K using WX5100 | |
| 3.5 Virgl On i5-4460(5700xt) | Virgl Performance on i5-4460 using 5700xt | |
| 3.6 Virgl On i7-9700K(5700xt) | Virgl Performance on i7-9700K using 5700xt | |
| i5-4460 | i7-9700K |
|---|
| glmark2 | 9140, 9117, 9117 | 9730, 9651, 9660 |
| Unigine_Valley FPS | 43, 42.4, 42.3 | 45.6, 45.0, 45.0 |
| Unigine_Valley Score | 1800, 1773, 1769 | 1906, 1884, 1884 |
| Unigine_Heaven FPS | 44.8 | 46.9 |
| Unigine_Heaven Score | 1130 | 1182 |
Conclusion:
- WX5100 behaves almost the same on both i5/i7 platforms.
- i5’s cpu power won’t be a bottleneck in WX5100 scenario.
| i5-4460 | i7-9700K |
|---|
| glmark2 | 13950, 14165, 14315 | 22134, 22256, 22150 |
| Unigine_Valley FPS | 105, 103.1, 102.9 | 168.7, 169.1, 168.5 |
| Unigine_Valley Score | 4391, 4315, 4304 | 7057, 7068, 7043 |
| Unigine_Heaven FPS | 167.0 | 171.1 |
| Unigine_Heaven Score | 4206 | 4311 |
| Unigine_Heaven FPS(4k) | 43 | 42.8 |
| Unigine_Heaven Score(4k) | 1083 | 1077 |
Conclusion:
- 5700xt runs smoother in i7 than on i5, perhaps i5 4th is too old for working together with 5700xt?(4 cores, bus width, etc).
- i5’s CPU/Memory becomes a bottleneck in 5700xt testing.
3.3 Virgl On i5-4460(WX5100)
| i5-4460 | Virgl on i5-4460 |
|---|
| glmark2 | 9140, 9117, 9117 | 2892, 2859, 2827 |
| Unigine_Valley FPS | 43, 42.4, 42.3 | 40.8, 40.5, 40.6 |
| Unigine_Valley Score | 1800, 1773, 1769 | 1707, 1694, 1699 |
| Unigine_Heaven FPS | 44.8 | 42.2 |
| Unigine_Heaven Score | 1130 | 1062 |
Conclusion:
- glmark2: Virgl is 31.3% of the baremetal performance.
- Unigine Valley/Unigine Heaven: Virgl performance almost the same as baremetal.
3.4 Virgl On i7-9700K(WX5100)
| i7-9700K | Virgl on i7-9700K |
|---|
| glmark2 | 9730, 9651, 9660 | 4274, 4262, 4320 |
| Unigine_Valley FPS | 45.6, 45.0, 45.0 | 42.3, 41.6, 41.5 |
| Unigine_Valley Score | 1906, 1884, 1884 | 1770, 1740, 1737 |
| Unigine_Heaven FPS | 46.9 | 41.9 |
| Unigine_Heaven Score | 1182 | 1055 |
Conclusion:
- glmark2: Virgl is 44.2% of the baremetal performance.
- Unigine Valley/Unigine Heaven: Virgl performance almost the same as baremetal.
- Comparing to 3.3: glmark2 will be improved using powerful CPU/Memory.
3.5 Virgl On i5-4460(5700xt)
| i5-4460 | Virgl on i5-4460 |
|---|
| glmark2 | 13950, 14165, 14315 | 2916, 3174, 2832 |
| Unigine_Valley FPS | 105, 103.1, 102.9 | 61, 61.9, 60.9 |
| Unigine_Valley Score | 4391, 4315, 4304 | 2551, 2588, 2548 |
| Unigine_Heaven FPS | 167.0 | 89.7 |
| Unigine_Heaven Score | 4206 | 2271 |
| Unigine_Heaven FPS(4k) | 43 | 37.8 |
| Unigine_Heaven Score(4k) | 1083 | 951 |
Conclusion:
- glmark2: Virgl is 21% of the baremetal performance.
- Unigine Valley/Unigine Heaven: Virgl is around 55%~60% of the baremetal performance, while in 4k behavior, 87% of the baremetal performance.
3.6 Virgl On i7-9700K(5700xt)
| i7-9700K | Virgl on i7-9700K |
|---|
| glmark2 | 22134, 22256, 22150 | 4152, 4256, 4238 |
| Unigine_Valley FPS | 168.7, 169.1, 168.5 | 91.6, 91.5, 91.4 |
| Unigine_Valley Score | 7057, 7068, 7043 | 3831, 3829, 3825 |
| Unigine_Heaven FPS | 171.1 | 85.3 |
| Unigine_Heaven Score | 4311 | 2149 |
| Unigine_Heaven FPS(4k) | 42.8 | 35.6 |
| Unigine_Heaven Score(4k) | 1077 | 896 |
Conclusion:
- glmark2: Virgl is 19% of the baremetal performance.
- Unigine Valley/Unigine Heaven: Virgl is around 55%~60% of the baremetal performance, while in 4k behavior, 83% of the baremetal performance.
4. Android Scenario
| Hardware/Platform | Score(scrcpy) | Score(no scrcpy) |
|---|
| i7-9700K+5700xt | 616521(剑侠山谷: 309760 , 禅院悟道: 306761) | 617133(剑侠山谷: 310050, 禅院悟道: 307083) |
| Virgl on (i7-9700K+5700xt) | 442043(剑侠山谷: 223850 , 禅院悟道: 218193) | 564343(剑侠山谷: 289202, 禅院悟道:275141) |
| i5-4460+5700xt | 384564(剑侠山谷: 112763 , 禅院悟道: 221801) | 592030(剑侠山谷: 283705, 禅院悟道: 308255) |
| Virgl on (i5-4460+5700xt) | 227747(剑侠山谷: 108206 , 禅院悟道: 119541) | 445234(剑侠山谷: 214831, 禅院悟道:230403) |
| i7-9700K+WX5100 | 567503(剑侠山谷: 265995 , 禅院悟道: 301508) | 585720(剑侠山谷: 277133, 禅院悟道: 308587) |
| Virgl on (i7-9700K+WX5100) | 412764(剑侠山谷: 210150 , 禅院悟道: 202614) | 499942(剑侠山谷: 257037, 禅院悟道: 242905) |
| i5-4460+WX5100 | 401626(剑侠山谷: 166695 , 禅院悟道: 234931) | 572952(剑侠山谷: 267744, 禅院悟道: 305208) |
| Virgl on (i5-4460+WX5100) | 225837(剑侠山谷: 106071 , 禅院悟道: 119766) | 445202(剑侠山谷: 211450, 禅院悟道:233752) |
Conclusion:
- Ludashi’s top score: around 61W, the maximum performance would be 1080p?
- scrcpy will greatly impact the performance when using Virgl under low-end CPU.
- virgl will be 85% for the best of bare metal on WX5100 on i7, 91% of bare metal on 5700xt on i7



